
Gary Kwong, GitHub: nth10sd or gkw@mozilla.com

the people writing and running fuzzers are by far the most effective QA people at Mozilla.
Nicholas Nethercote, MemShrink & Low Level Tools Team Manager at Mozilla
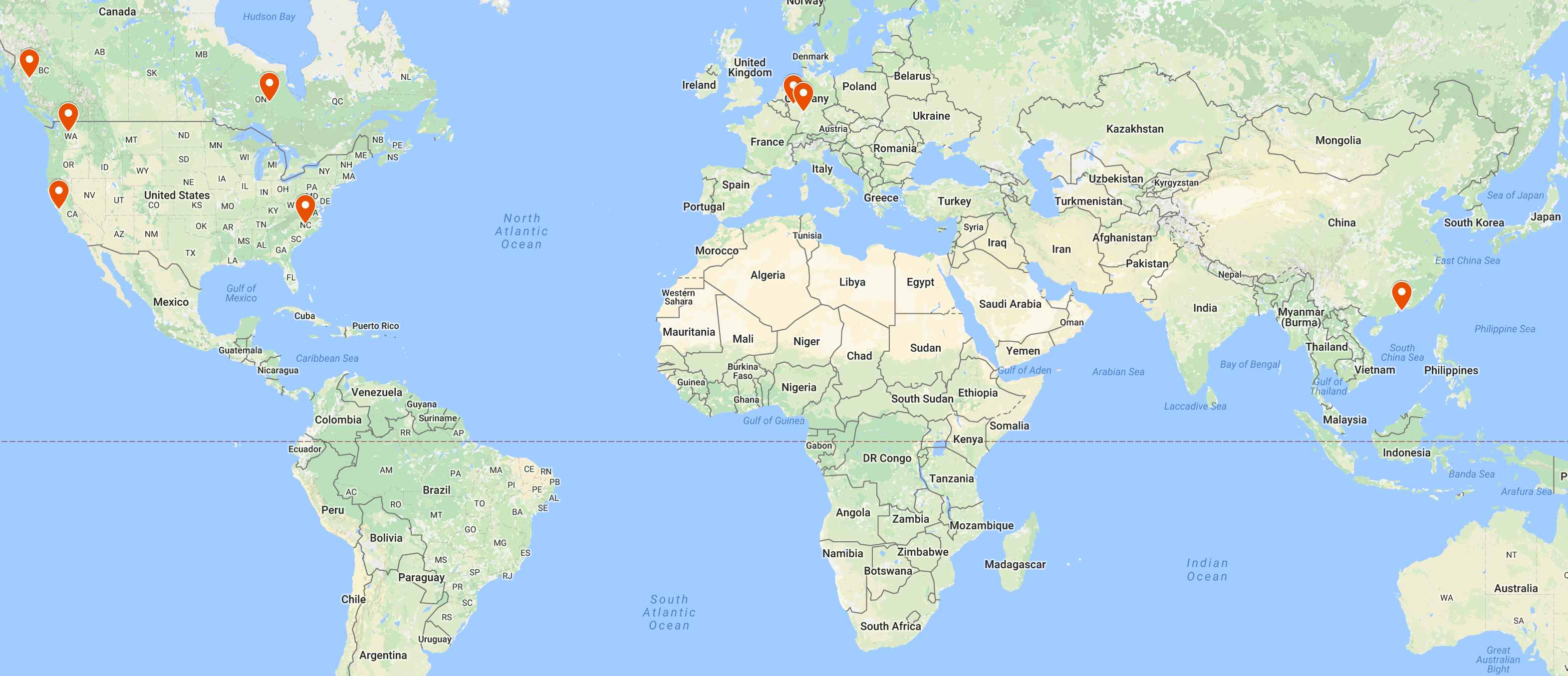
Fuzzing is an effective way to find corner cases overlooked when creating a patch and a test for it. A comprehensive fuzz bug report can also provide more information on how to fix it.
[:arai] Mozilla community contributor
